10 Essential Practices for Effective API Cybersecurity

10 Essential Practices for Effective API Cybersecurity
Introduction
As organizations increasingly rely on APIs for data exchange, these interfaces have become prime targets for cyberattacks. This shift highlights the urgent need for effective cybersecurity practices. In this article, we will explore ten essential strategies that organizations can implement to safeguard their APIs. These strategies not only protect sensitive information but also help maintain user trust and ensure regulatory compliance.
Given the evolving landscape of API vulnerabilities, businesses must ask: how can they stay ahead of potential threats and fortify their defenses? By exploring these critical practices, we will uncover actionable insights that can significantly enhance API security and resilience. Understanding these strategies is vital for any organization looking to protect its data and uphold its reputation in an increasingly digital world.
Initial Data Offering: Secure Your Data Marketplace with Robust API Practices
The Initial Information Offering (IDO) acts as a centralized hub for information exchange, making robust API cybersecurity practices essential. Why is API security so crucial? By securing APIs, IDO not only protects sensitive information but also maintains user trust and ensures compliance with regulations. This involves adopting best practices that safeguard the integrity and confidentiality of transactions.
The advantages of implementing these security measures are significant. They enhance the platform's reputation and foster user engagement. When users feel their data is secure, they are more likely to interact with the platform confidently.
In conclusion, prioritizing API cybersecurity is not just a technical requirement; it’s a strategic advantage. Organizations should consider how these practices can be integrated into their operations to protect their assets and build lasting trust with their users.
OWASP API Security Top 10 2023: Identify and Mitigate Key Vulnerabilities
The OWASP API Cybersecurity Top 10 for 2023 highlights critical vulnerabilities that businesses must address to ensure effective API cybersecurity for their APIs. Among these, Broken Object Level Authorization (BOLA) and Broken Authentication stand out, as they can lead to unauthorized access and significant data breaches. By implementing robust authentication protocols, such as validating JWT tokens at the API gateway, and enforcing strict access controls, organizations can effectively combat these risks.
A recent survey reveals that only 32% of organizations have fully integrated OWASP guidelines into their protective practices. This statistic underscores the urgent need for enhancement in security measures. Consistently assessing and refreshing protective strategies in line with OWASP recommendations is vital for reducing risks and safeguarding sensitive information. How can your organization ensure it is not part of the 68% that fall short?
Cybersecurity experts emphasize the importance of proactive steps, such as:
- Validating user input
- Utilizing multi-factor authentication
These steps are crucial in strengthening API cybersecurity to protect against evolving threats. Additionally, continuous API discovery and lifecycle management are essential strategies for maintaining security. By prioritizing these vulnerabilities and adhering to best practices, organizations can significantly bolster their API cybersecurity posture.
Implement Strong Authentication and Authorization Mechanisms
To effectively secure APIs, organizations must adopt robust authentication mechanisms that contribute to API cybersecurity, such as OAuth 2.0 and OpenID Connect. These protocols ensure that only authorized users can access sensitive information, significantly reducing the risk of unauthorized entry. For instance, OAuth 2.0 allows applications to securely access user data without exposing passwords. Meanwhile, OpenID Connect builds on this by providing identity verification, which enhances user trust.
Incorporating multi-factor authentication (MFA) further enhances protection by requiring users to provide multiple forms of verification before gaining access. This additional layer makes it considerably more challenging for unauthorized users to breach systems. Current trends indicate that 87% of large entities implement MFA, reflecting a growing recognition of its importance in safeguarding digital assets. Moreover, with over 99.9% of compromised accounts lacking MFA, its adoption is crucial for mitigating risks associated with cyber threats.
Security analysts emphasize that implementing MFA is not just a best practice but a necessity in today’s threat landscape. As cyberattacks become increasingly sophisticated, the integration of OAuth 2.0, OpenID Connect, and MFA is essential for API cybersecurity, as well as for maintaining the integrity and confidentiality of API interactions. By remaining informed about safety protocols and trends, organizations can improve their API cybersecurity to better safeguard their APIs and sensitive information from evolving threats.
How can your organization leverage these authentication mechanisms to enhance security? By understanding the features, advantages, and benefits of these protocols, you can take proactive steps to protect your digital assets.
Conduct Regular Security Testing and Vulnerability Assessments
Organizations should conduct regular safety testing, including penetration testing and vulnerability assessments, to identify weaknesses in their API cybersecurity. This ongoing process is essential for a continuous protection strategy in API cybersecurity, enabling teams to promptly address vulnerabilities and ensure that APIs remain secure against evolving threats. Cybersecurity experts stress that consistent vulnerability assessments are vital for maintaining API cybersecurity. For example, Chandan Kumar Sahoo, CEO and Founder of Qualysec, emphasizes, "the sooner you detect a problem, the easier (and cheaper) it is to remediate." He further asserts, "Without a comprehensive API cybersecurity audit, protection is not an option - it is a necessity for the integrity of your digital operation." This underscores the financial and operational benefits of early detection.
Organizations are increasingly aware of the importance of frequent assessments. Currently, 32% conduct them annually or bi-annually, while 51% choose to outsource to third-party specialists. Looking ahead to 2025, this trend is expected to continue, with many entities adopting a quarterly testing schedule to stay ahead of potential breaches. Additionally, the integration of AI tools in vulnerability assessments is on the rise, with 75% of respondents in a recent report indicating they have embraced new AI technologies to enhance their testing processes. These AI tools automate reconnaissance, prioritize vulnerabilities, and simulate attack paths, significantly improving the efficiency of assessments.
Moreover, recent trends show that evaluations of API cybersecurity are becoming more comprehensive, focusing on identifying misconfigurations and vulnerabilities that could lead to data breaches. As organizations face increasing pressure to comply with regulations, the importance of routine vulnerability evaluations cannot be overstated. By prioritizing these evaluations, organizations can substantially reduce their risk exposure and bolster their overall defensive posture. Notably, the average cost of a penetration test is around $18,300, highlighting the significant investment organizations are making in their security measures.
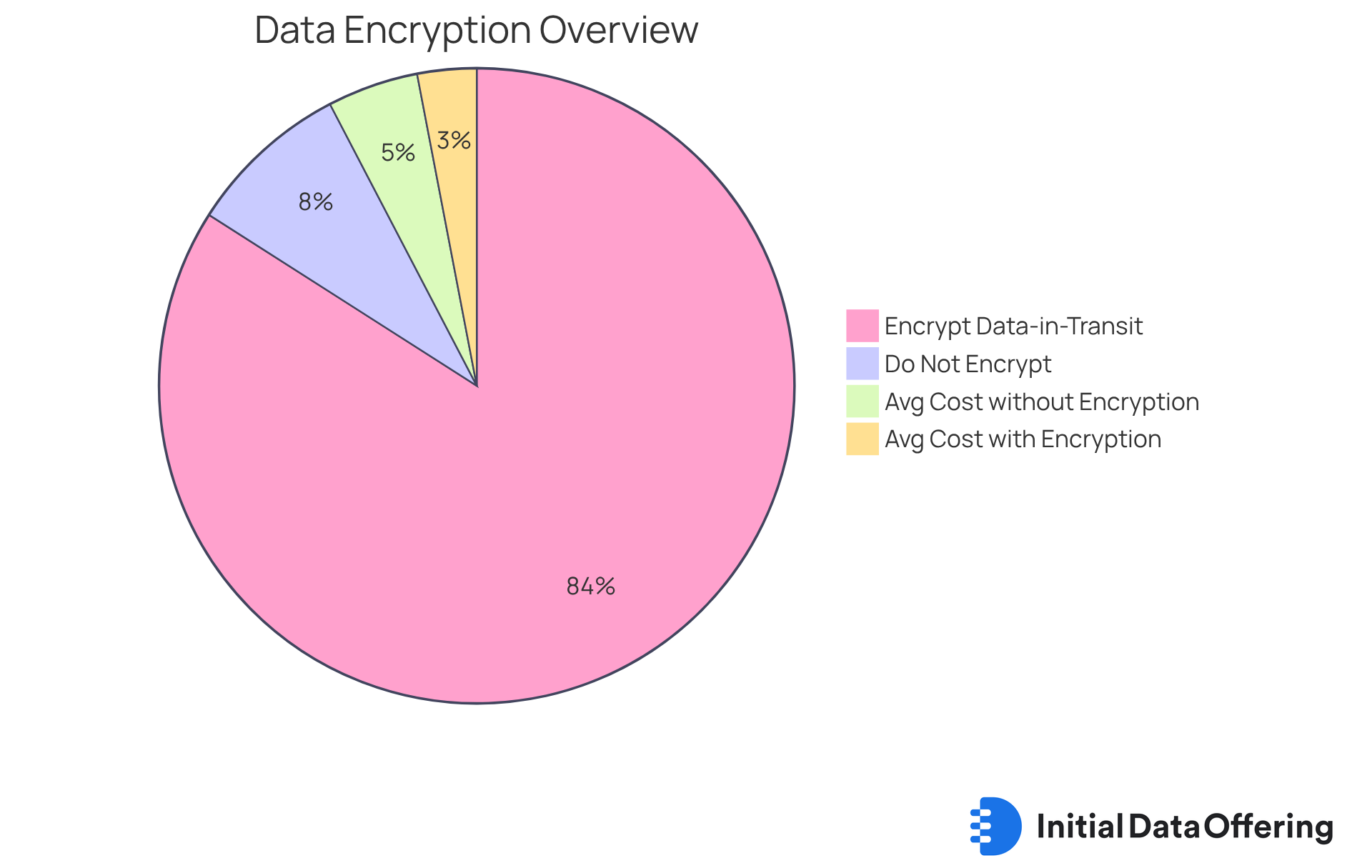
Utilize Data Encryption for Secure API Communication
To protect information in transit, organizations must implement encryption protocols like TLS (Transport Layer Security). This protocol ensures API cybersecurity by securing the data exchanged between clients and APIs, effectively preventing interception by unauthorized parties. Did you know that 91% of enterprises encrypt data-in-transit? This statistic reinforces the critical role of TLS in ensuring API cybersecurity. Furthermore, 93.2% of browsing sessions in Chrome utilize secure HTTPS connections, underscoring the widespread adoption of TLS for enhanced security.
However, encrypting sensitive data at rest is equally vital. It protects against unauthorized access and potential breaches. Financial services entities that implement comprehensive encryption strategies report significantly lower remediation expenses, averaging $3.26 million compared to $5.02 million for those lacking encryption. By prioritizing TLS and strong encryption practices, along with ongoing monitoring, organizations can significantly enhance their API cybersecurity measures and safeguard sensitive information from evolving cyber threats.
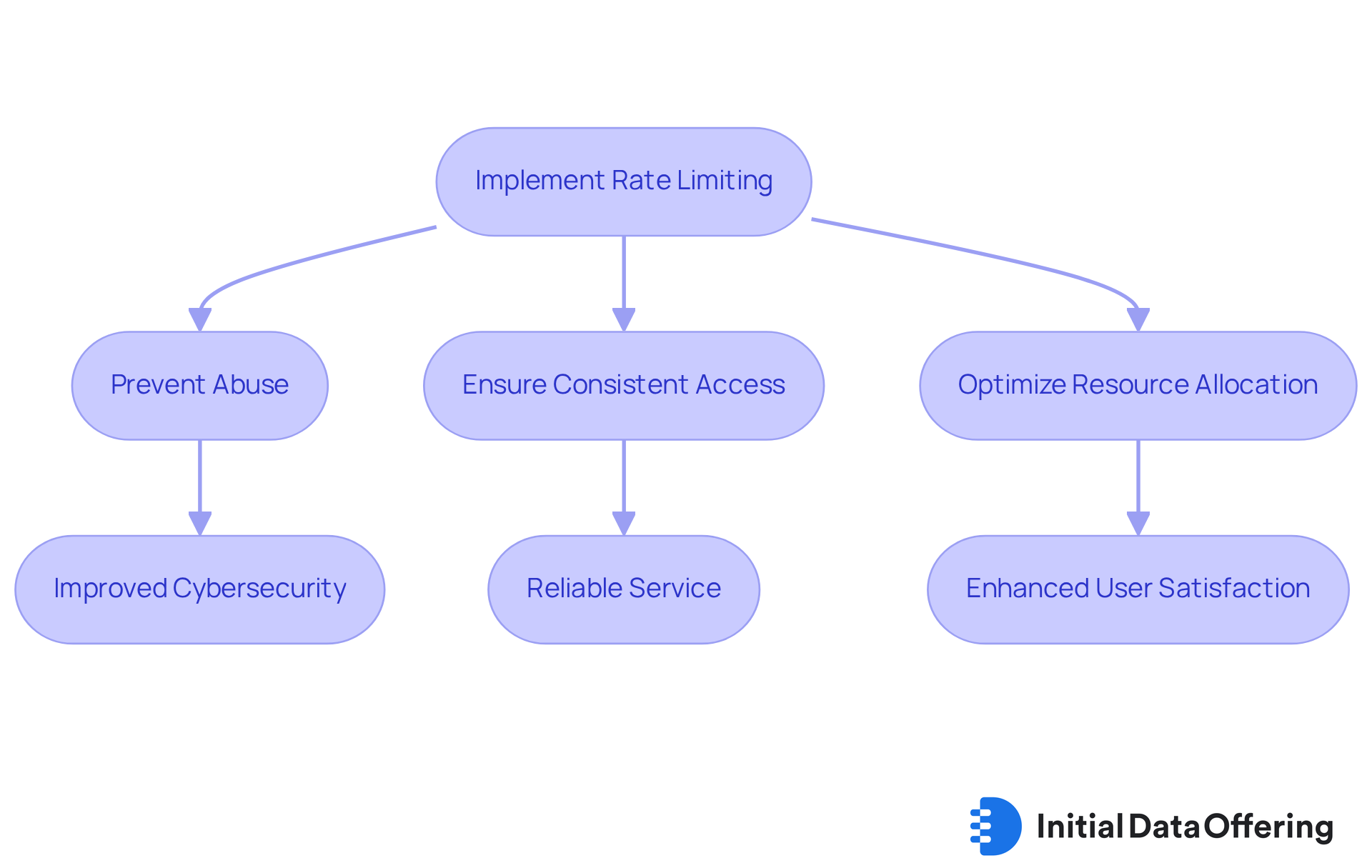
Implement Rate Limiting to Prevent Abuse and Overload
Implementing rate limiting is a crucial feature for businesses aiming to manage API traffic effectively and ensure API cybersecurity. This approach not only prevents abuse but also ensures that legitimate users have consistent access to resources. By setting specific limits on the number of requests per user or IP address, organizations can improve their API cybersecurity by protecting their APIs from overload, which is a significant advantage in maintaining optimal performance.
But why is this important? The benefits of rate limiting extend beyond just preventing abuse. It helps in optimizing resource allocation, ensuring that all users experience reliable service without interruptions. For instance, consider a scenario where a sudden spike in traffic could overwhelm an API. By implementing rate limiting, businesses can strengthen API cybersecurity to mitigate this risk, leading to improved user satisfaction and trust.
In conclusion, implementing rate limiting is not just a technical measure; it’s a strategic advantage that enhances the overall user experience. How might your organization benefit from adopting this practice? By considering the implications of rate limiting, you can better prepare your API infrastructure for future demands.
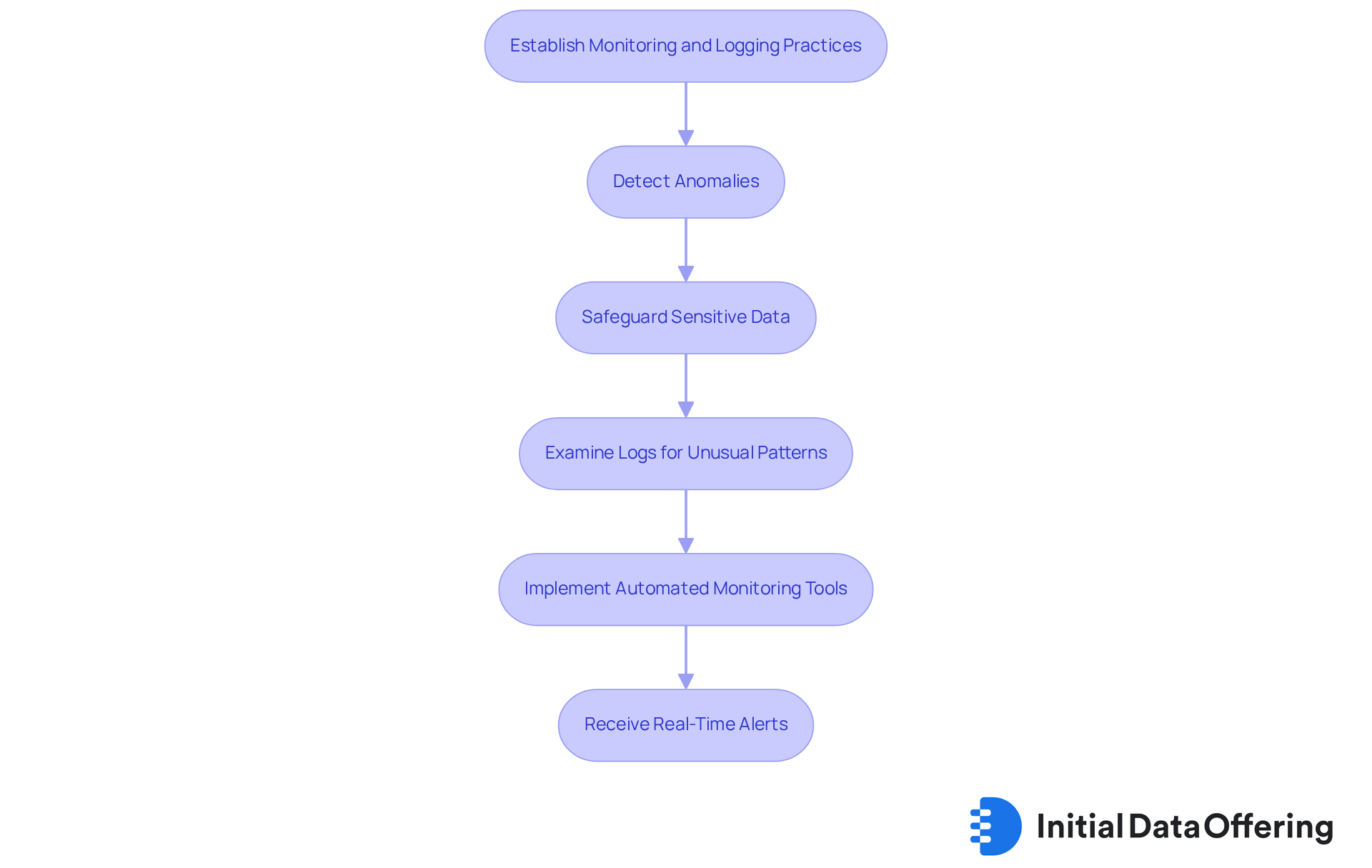
Establish Comprehensive Monitoring and Logging Practices
Organizations should establish comprehensive monitoring and logging practices to ensure effective API cybersecurity and track API usage. These practices not only help in detecting anomalies but also play a crucial role in safeguarding sensitive data. By examining logs for unusual patterns, monitoring teams can identify potential threats to API cybersecurity swiftly, which is essential for reducing risks.
Implementing automated monitoring tools enhances this process significantly. These tools provide real-time alerts for suspicious activities, allowing teams to react promptly. Imagine having the ability to catch a potential breach before it escalates - this is the power of proactive monitoring.
In conclusion, investing in robust monitoring and logging practices is not just a technical necessity; it’s a strategic advantage. Organizations that prioritize these measures can better protect their assets and maintain trust with their users. How prepared is your organization to handle threats related to API cybersecurity?
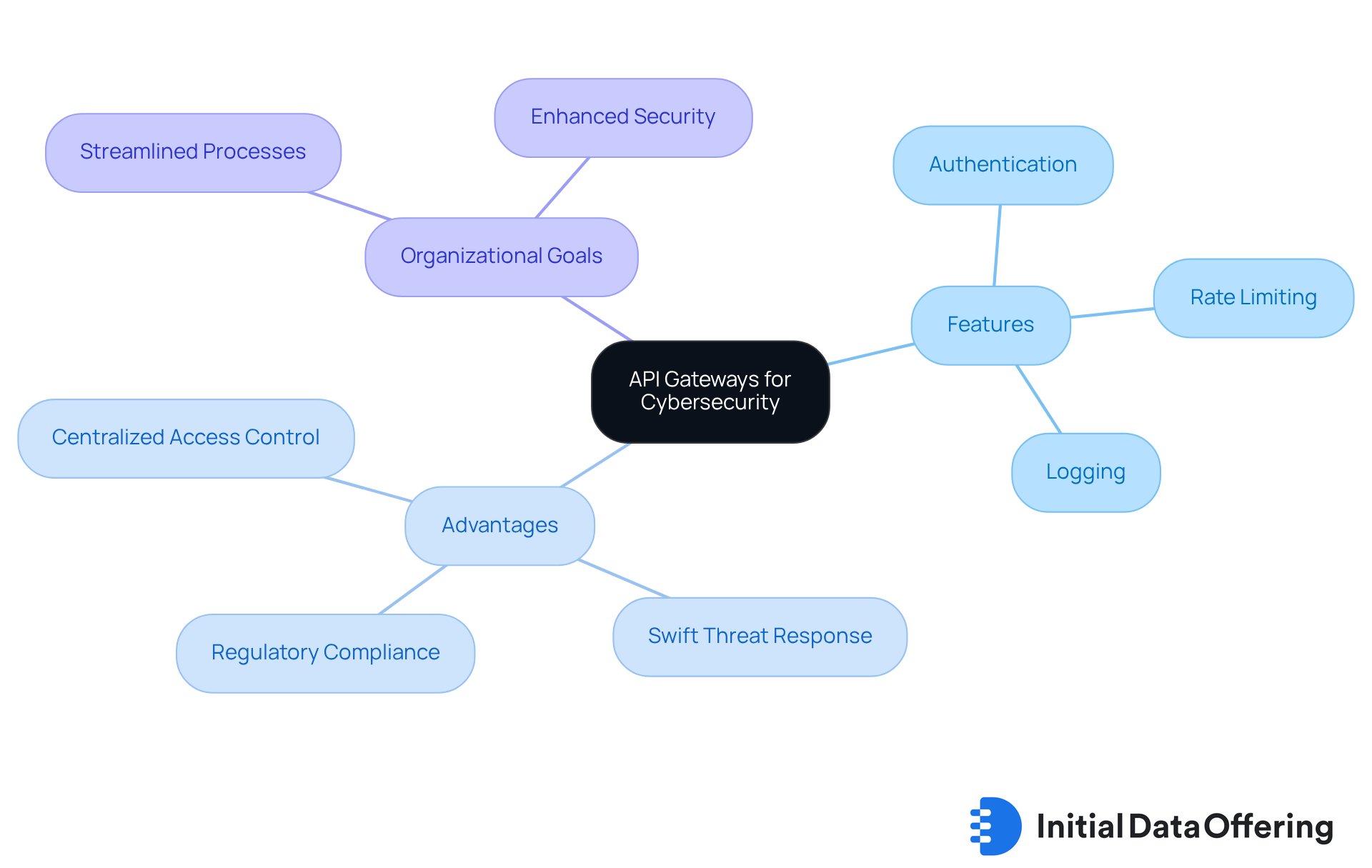
Leverage API Gateways for Enhanced Security Management
API gateways serve a crucial function in enhancing API cybersecurity by providing a centralized platform for managing access and enforcing safety policies. What makes API gateways so vital? They allow organizations to implement consistent protective measures across all APIs, which are essential for API cybersecurity and include features like authentication, rate limiting, and logging. This uniformity not only simplifies management but also strengthens security protocols across the board.
The advantages of utilizing API gateways extend beyond mere management. By centralizing access control and implementing API cybersecurity measures, organizations can respond more swiftly to security threats and ensure compliance with regulations. This proactive approach to API management enhances API cybersecurity, leading to a more secure environment for data exchange and ultimately benefiting the organization as a whole.
In conclusion, adopting API gateways is not just about protection; it’s about creating a robust framework that supports organizational goals. As you consider your API strategy, think about how implementing an API gateway could streamline your processes and enhance security. Are you ready to take your API management to the next level?
Train Employees on API Security Best Practices
Organizations should invest in training programs that inform employees about best practices for API cybersecurity. These programs feature essential components such as:
- Understanding common threats
- Recognizing phishing attempts
- Adhering to secure coding practices
The advantage of regular training sessions lies in their ability to strengthen awareness of API cybersecurity, ensuring that all team members are equipped to contribute effectively to protecting APIs.
Studies reveal that entities with efficient awareness training (SAT) programs are 8.3 times less likely to appear on public data breach lists each year. This statistic underscores the urgent need for thorough training, particularly as incidents related to API cybersecurity have surged from 78% in 2023 to a record high of 84% in 2024. Regular training can significantly reduce risk from 60% to 10% within the first 12 months, highlighting its effectiveness in safeguarding organizations.
As Mike Jenkins, President of BrickTech, aptly stated, "Employees are a business’s first line of defense against cyber threats." By promoting a culture of awareness, companies can greatly mitigate risks associated with API vulnerabilities and enhance their overall API cybersecurity posture. How prepared is your organization to face these challenges? Investing in training not only protects your assets but also empowers your workforce.
Maintain Regular Updates and Patching for API Security
To ensure robust API cybersecurity, organizations must establish a routine for regular updates and patching. This practice involves actively monitoring for new vulnerabilities and promptly applying patches to mitigate potential risks. By staying current with security updates, companies can effectively enhance their API cybersecurity and shield their APIs from known threats, significantly improving their overall security posture.
Why is this important? Regular updates not only address existing vulnerabilities but also fortify defenses against emerging threats. The advantage of this proactive approach lies in its ability to reduce the likelihood of security breaches, which can lead to costly repercussions. Ultimately, the benefit is clear: a well-maintained API cybersecurity environment fosters trust and reliability, which are essential for any organization operating in today’s digital landscape.
Incorporating a routine for updates and patching is not just a technical necessity; it’s a strategic imperative for API cybersecurity. How can your organization implement such practices effectively? Consider establishing a dedicated team to oversee this process, ensuring that your APIs remain secure and resilient against evolving threats.
Conclusion
Prioritizing effective API cybersecurity is essential for organizations aiming to protect sensitive data and maintain user trust. What if your organization could not only safeguard its assets but also enhance its operational integrity? By implementing robust security practices, businesses achieve both goals. The strategies outlined, from strong authentication mechanisms to regular security assessments, provide a comprehensive framework for mitigating risks associated with API vulnerabilities.
The article emphasizes several key practices, including:
- The integration of OWASP guidelines
- The necessity of data encryption
- The implementation of rate limiting
Each of these elements plays a crucial role in fortifying an organization’s defenses against cyber threats. Consider this: continuous training and updates ensure that teams remain vigilant and prepared to tackle emerging challenges in the API landscape.
In a world where cyber threats are increasingly sophisticated, organizations must take proactive measures to secure their APIs. By embracing these essential practices, businesses can protect their digital assets and foster a culture of security awareness. This commitment to API cybersecurity is not merely a technical obligation; it is a strategic advantage that can significantly impact an organization’s reputation and success in the digital marketplace.
Frequently Asked Questions
What is the purpose of the Initial Data Offering (IDO)?
The IDO acts as a centralized hub for information exchange, making robust API cybersecurity practices essential to protect sensitive information, maintain user trust, and ensure compliance with regulations.
Why is API security crucial for organizations?
API security is crucial because it safeguards the integrity and confidentiality of transactions, protects sensitive information, maintains user trust, and ensures compliance with regulations.
What are the benefits of implementing robust API security measures?
Implementing robust API security measures enhances the platform's reputation, fosters user engagement, and encourages users to interact confidently with the platform, knowing their data is secure.
What are the key vulnerabilities highlighted in the OWASP API Security Top 10 for 2023?
Key vulnerabilities include Broken Object Level Authorization (BOLA) and Broken Authentication, which can lead to unauthorized access and significant data breaches.
How can organizations combat risks associated with API vulnerabilities?
Organizations can combat risks by implementing robust authentication protocols, such as validating JWT tokens at the API gateway, enforcing strict access controls, and adopting proactive security measures like validating user input and utilizing multi-factor authentication.
What percentage of organizations have fully integrated OWASP guidelines into their protective practices?
Only 32% of organizations have fully integrated OWASP guidelines into their protective practices, indicating a need for enhancement in security measures.
What authentication mechanisms should organizations adopt to secure APIs?
Organizations should adopt robust authentication mechanisms such as OAuth 2.0 and OpenID Connect, which help ensure that only authorized users can access sensitive information.
How does multi-factor authentication (MFA) contribute to API security?
MFA enhances protection by requiring users to provide multiple forms of verification before gaining access, making it significantly more challenging for unauthorized users to breach systems.
What current trend indicates the importance of MFA in organizations?
Current trends show that 87% of large entities implement MFA, reflecting a growing recognition of its importance in safeguarding digital assets.
Why is it essential for organizations to remain informed about safety protocols and trends in API cybersecurity?
Remaining informed about safety protocols and trends is essential for organizations to improve their API cybersecurity and better safeguard their APIs and sensitive information from evolving threats.