10 Essential Items for Your Small Business Cybersecurity Checklist

10 Essential Items for Your Small Business Cybersecurity Checklist
Introduction
In today's digital landscape, small businesses encounter a multitude of cyber threats that can compromise their operations and erode customer trust. This article outlines ten essential items that should be included in every small business's cybersecurity checklist. By implementing these practical strategies, businesses can strengthen their defenses against potential breaches.
But with so many options available, how can organizations identify which measures are truly effective in protecting their sensitive data and ensuring business continuity? Understanding the features, advantages, and benefits of each strategy is crucial. This exploration will not only highlight the importance of cybersecurity but also provide actionable insights for small businesses to enhance their security posture.
Initial Data Offering: Access Unique Datasets for Cybersecurity Insights
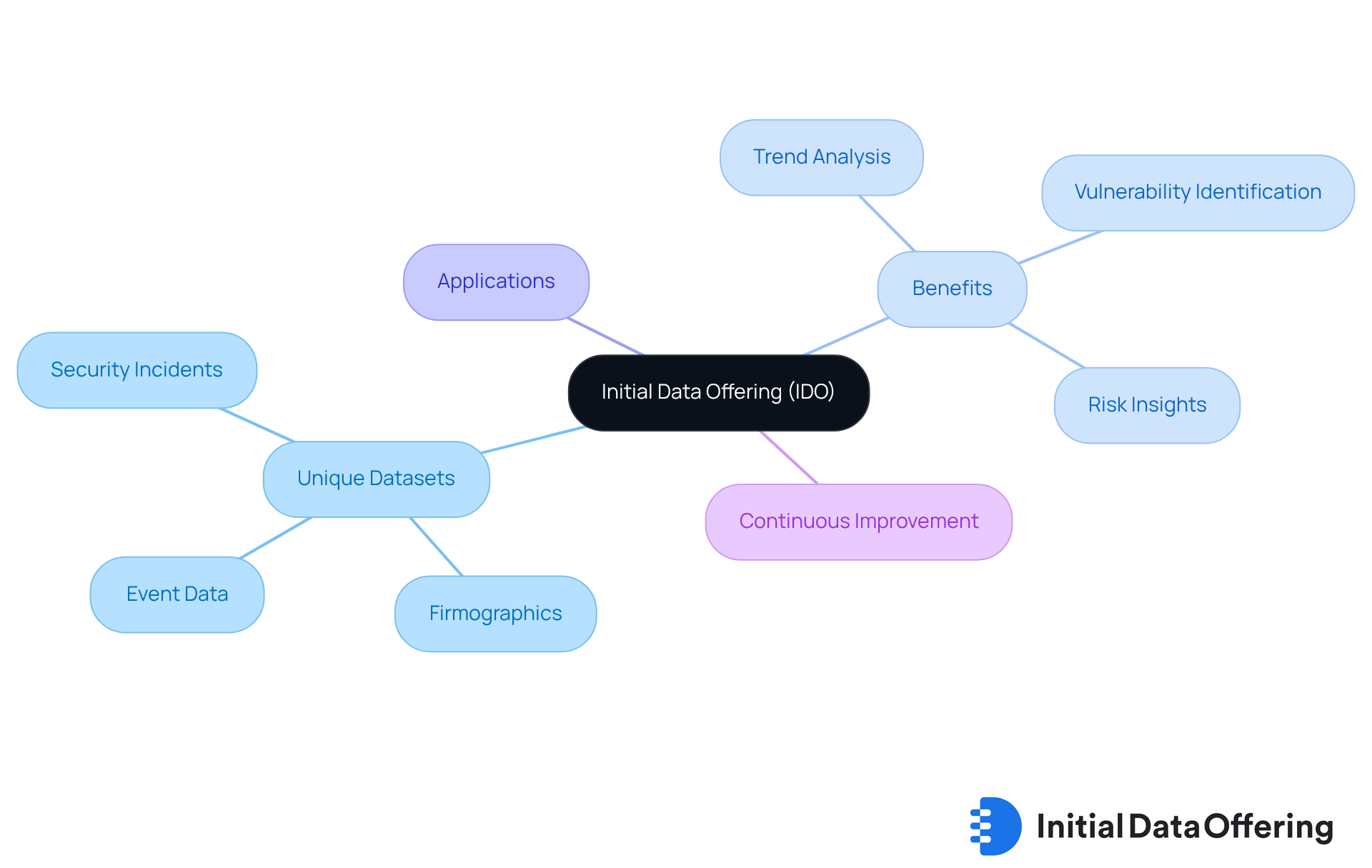
Initial Data Offering (IDO) serves as a vital resource for small enterprises looking to enhance their security protocols. What if you could access unique datasets that reveal critical insights into your security landscape? IDO provides access to distinctive datasets, including comprehensive firmographics and event data. This allows companies to analyze trends, identify vulnerabilities, and understand the evolving landscape of cyber threats.
For instance, datasets related to security incidents enable organizations to evaluate their protective measures against industry benchmarks. This comparison not only highlights areas for improvement but also fosters a proactive approach to security. Additionally, alternative data can unveil insights into potential risks associated with third-party suppliers, which is crucial for maintaining a robust security posture.
By leveraging these datasets, organizations can make informed, data-driven decisions that bolster their security frameworks. Ultimately, this enhances their resilience against emerging threats. How can your organization utilize these insights to strengthen its defenses? Embracing IDO not only empowers businesses to stay ahead of cyber threats but also fosters a culture of continuous improvement in security practices.
Develop a Comprehensive Cybersecurity Policy
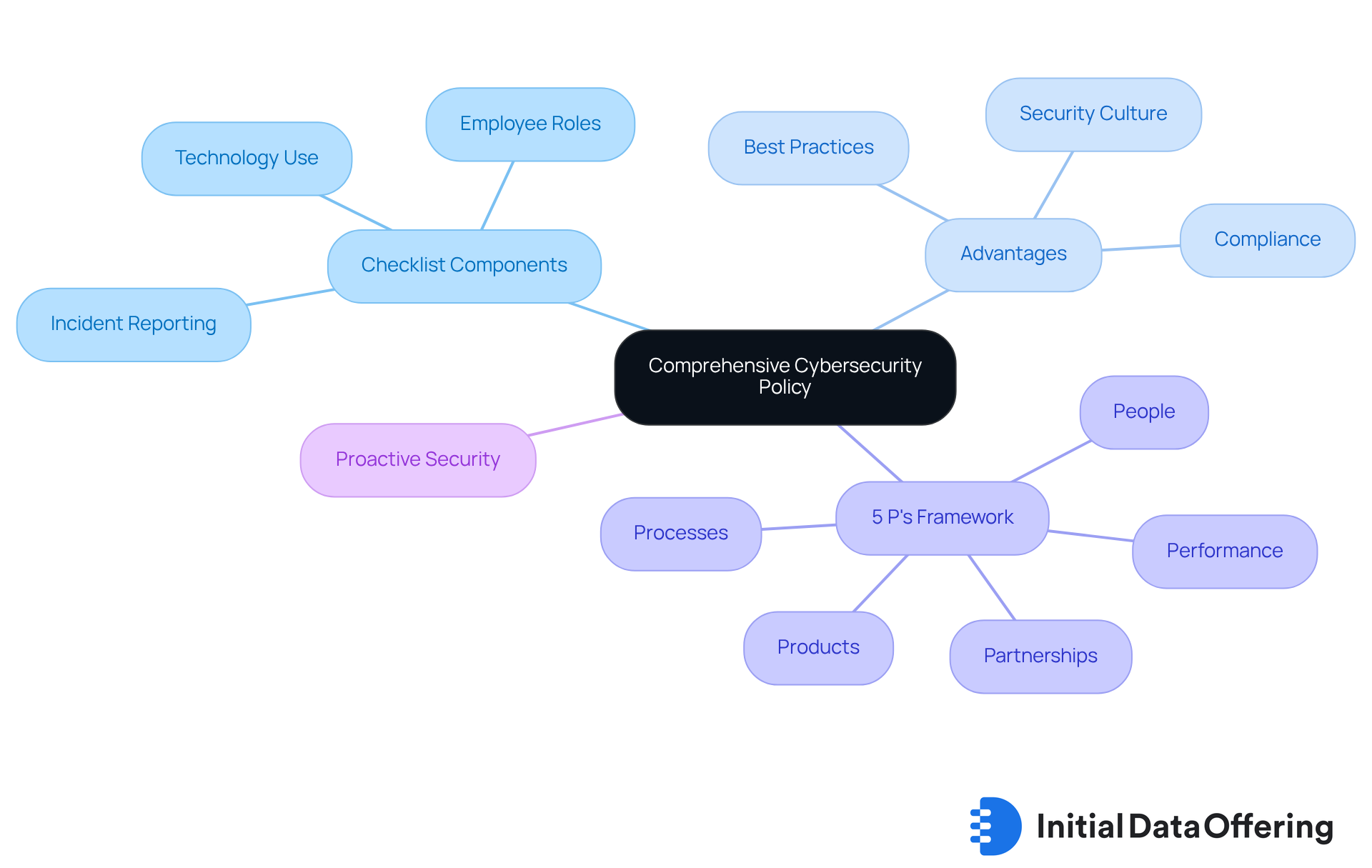
Creating a thorough small business cybersecurity checklist is essential for small enterprises. It sets clear guidelines and expectations for data protection. This policy should define employee roles and responsibilities, outline acceptable technology use, and detail procedures for reporting incidents.
What are the advantages of having such a policy? It incorporates best practices for data handling and storage, ensuring compliance with relevant regulations like GDPR. Frequent assessments and revisions to the policy are crucial to adapt to emerging threats and changes in the market landscape. By promoting a culture of security awareness and responsibility, small enterprises can significantly strengthen their resilience against cyber threats, which is crucial according to the small business cybersecurity checklist.
Consider this: research shows that around 60% of small enterprises that face a cyber attack cease operations within six months. This statistic highlights the importance of developing a strong security policy as part of a small business cybersecurity checklist. Additionally, integrating the 5 P's of the security framework - People, Processes, Products, Partnerships, and Performance - provides a structured approach to policy development.
Expert insights emphasize that digital security should be a proactive initiative. Regular policy reviews are essential, especially since 50% of SMBs indicate that recovery from a cyberattack takes 24 hours or more. By understanding these elements, small enterprises can better prepare themselves against potential cyber threats.
Implement Regular Employee Cybersecurity Training
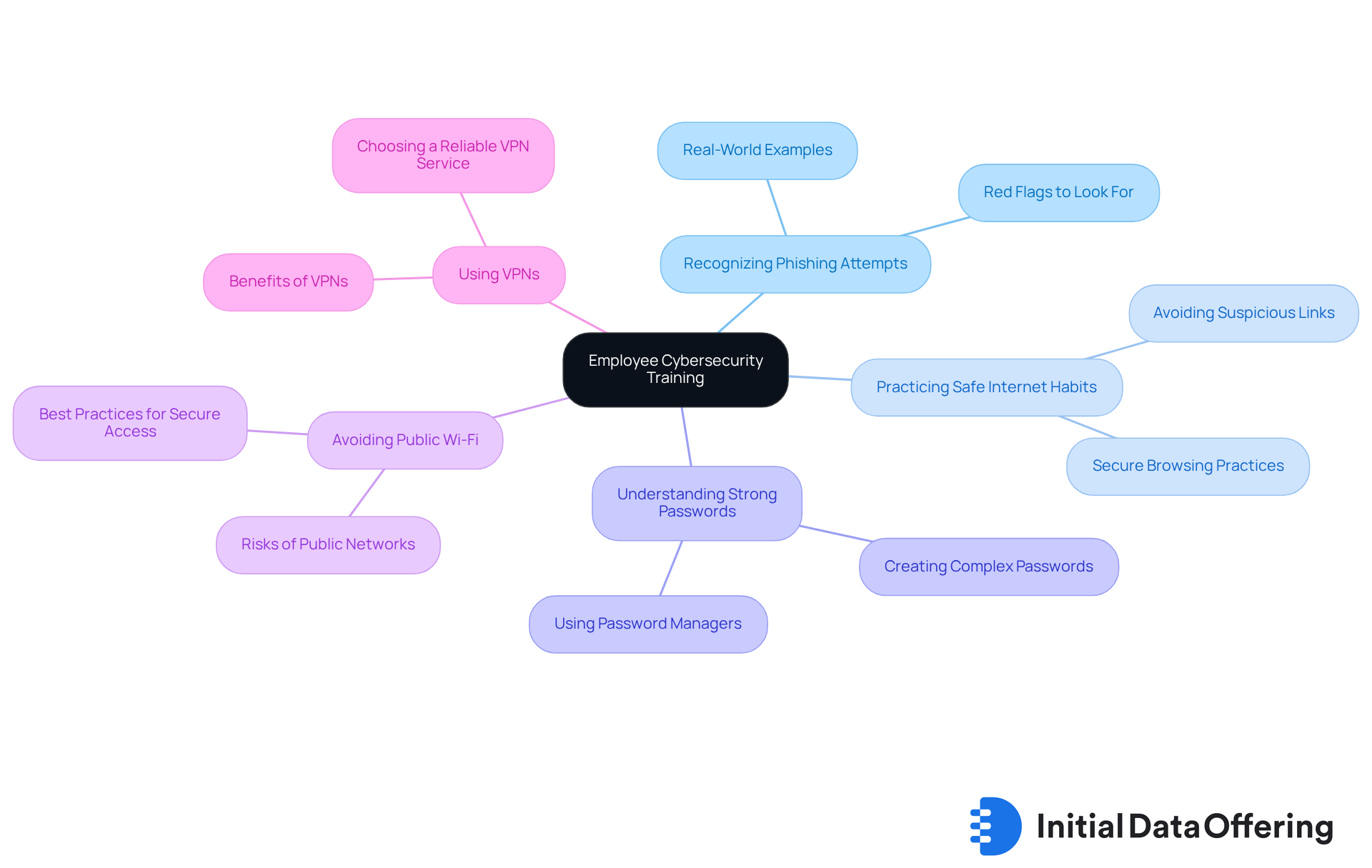
Conducting regular cybersecurity training for staff is a proactive measure that significantly reduces the risk of breaches. This training encompasses essential topics such as:
- Recognizing phishing attempts
- Practicing safe internet habits
- Understanding the importance of strong passwords
- Avoiding accessing sensitive information over public Wi-Fi
- The necessity of using Virtual Private Networks (VPNs) to secure their connections
Interactive sessions and simulations not only enhance engagement but also improve the retention of information. By fostering a culture of awareness, businesses empower employees to act as the first line of defense against cyber threats. Have you considered how well your team can identify potential phishing attempts? Studies show that organizations with robust security awareness training programs experience a 50% reduction in successful phishing attacks, highlighting the effectiveness of these initiatives.
The financial implications of data breaches are substantial, with the average cost soaring to $4.4 million. This statistic underscores the financial rationale for investing in cybersecurity training. Ongoing training is crucial to keep employees informed about evolving threats and best practices, as highlighted in the small business cybersecurity checklist, ensuring they are well-equipped to handle potential cyber incidents effectively. How prepared is your organization to face these challenges?
Enforce Strong Password Policies and Multi-Factor Authentication
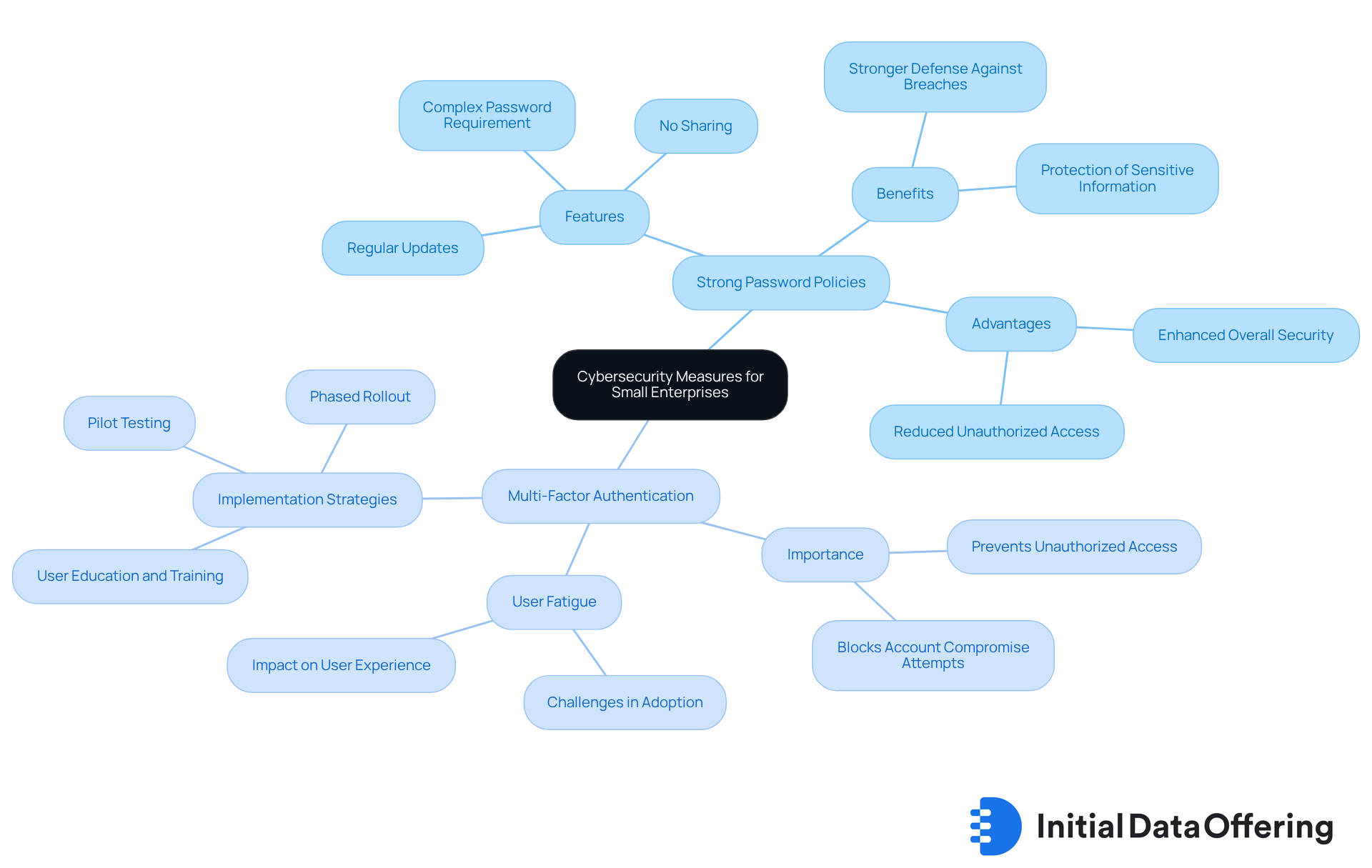
Implementing robust password policies is essential for safeguarding sensitive information in small enterprises. Features of these policies include the requirement for employees to create complex passwords, regularly update them, and refrain from sharing them. Advantages of such measures are significant; they reduce the likelihood of unauthorized access and enhance overall security. Benefits include a stronger defense against potential breaches, which is crucial in today’s digital landscape.
In addition to strong password policies, incorporating multi-factor authentication (MFA) greatly enhances protection. MFA requires users to verify their identity through multiple methods, creating a dual-layer security approach. This method not only minimizes the risk of unauthorized access but also plays a vital role in preventing security breaches. According to experts in digital protection, MFA can prevent up to 99.2% of account compromise attempts, making it a critical component of any security strategy. As one analyst noted, 'MFA is a straightforward, intelligent security enhancement' that bolsters the overall safety of small enterprises.
Organizations should also establish backup authentication procedures for users who may lose access to their primary MFA devices. With 68% of individuals needing to change their passwords at least once a year due to compromised credentials, the importance of strong password policies alongside MFA cannot be overstated. However, it’s crucial for organizations to recognize potential user fatigue associated with MFA, which can hinder its adoption. How can organizations ensure effective implementation? Conducting pilot tests with small user groups before a full rollout is a recommended strategy.
Given the increasing frequency of cyberattacks, implementing MFA is not just beneficial but necessary for protecting both company and customer data. By prioritizing the measures in a small business cybersecurity checklist, small enterprises can significantly enhance their defense against evolving threats.
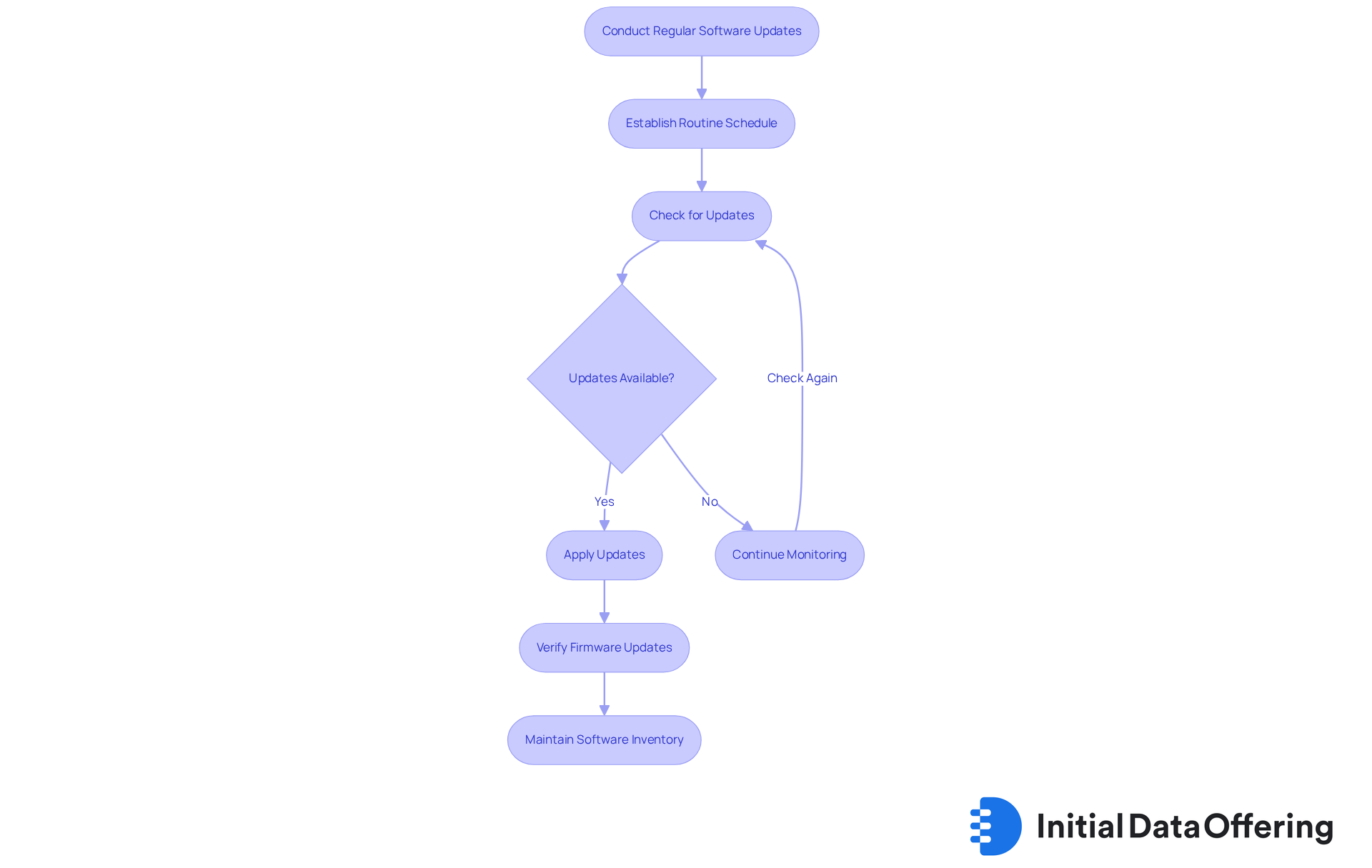
Conduct Regular Software Updates and Patch Management
Regular software updates and effective patch management are crucial components of a robust cybersecurity strategy for small enterprises. Establishing a routine schedule for checking and applying updates across all software applications and operating systems is vital. This proactive approach helps close vulnerabilities that cybercriminals may exploit. Additionally, companies should not overlook the importance of verifying firmware updates for devices like routers and smart home gadgets, as these can also serve as entry points for attacks. Maintaining an inventory of all software in use ensures that no application is neglected, significantly reducing the risk of vulnerabilities.
The impact of patch management on the safety of small enterprises cannot be overstated. Timely updates not only protect against known threats but also enhance overall system performance. Best practices include:
- Enabling automatic updates whenever possible, allowing for seamless integration of security patches without manual intervention.
- Cybersecurity analysts, including Dr. Chris Pierson, stress that neglecting these updates can lead to severe consequences, as outdated software is a prime target for attackers. Dr. Pierson notes, "These patches address known vulnerabilities in the software, effectively closing doors that could be exploited by attackers."
Current trends show a growing focus on automated patch management solutions, which streamline the update process and ensure compliance with industry standards. By adopting these strategies, especially during Cybersecurity Awareness Month, small businesses can refer to a small business cybersecurity checklist to strengthen their defenses against evolving cyber threats and maintain a secure digital environment.
Have you considered how automated patch management could simplify your cybersecurity efforts? By implementing these practices, you not only protect your systems but also enhance operational efficiency.
Establish a Reliable Data Backup Strategy
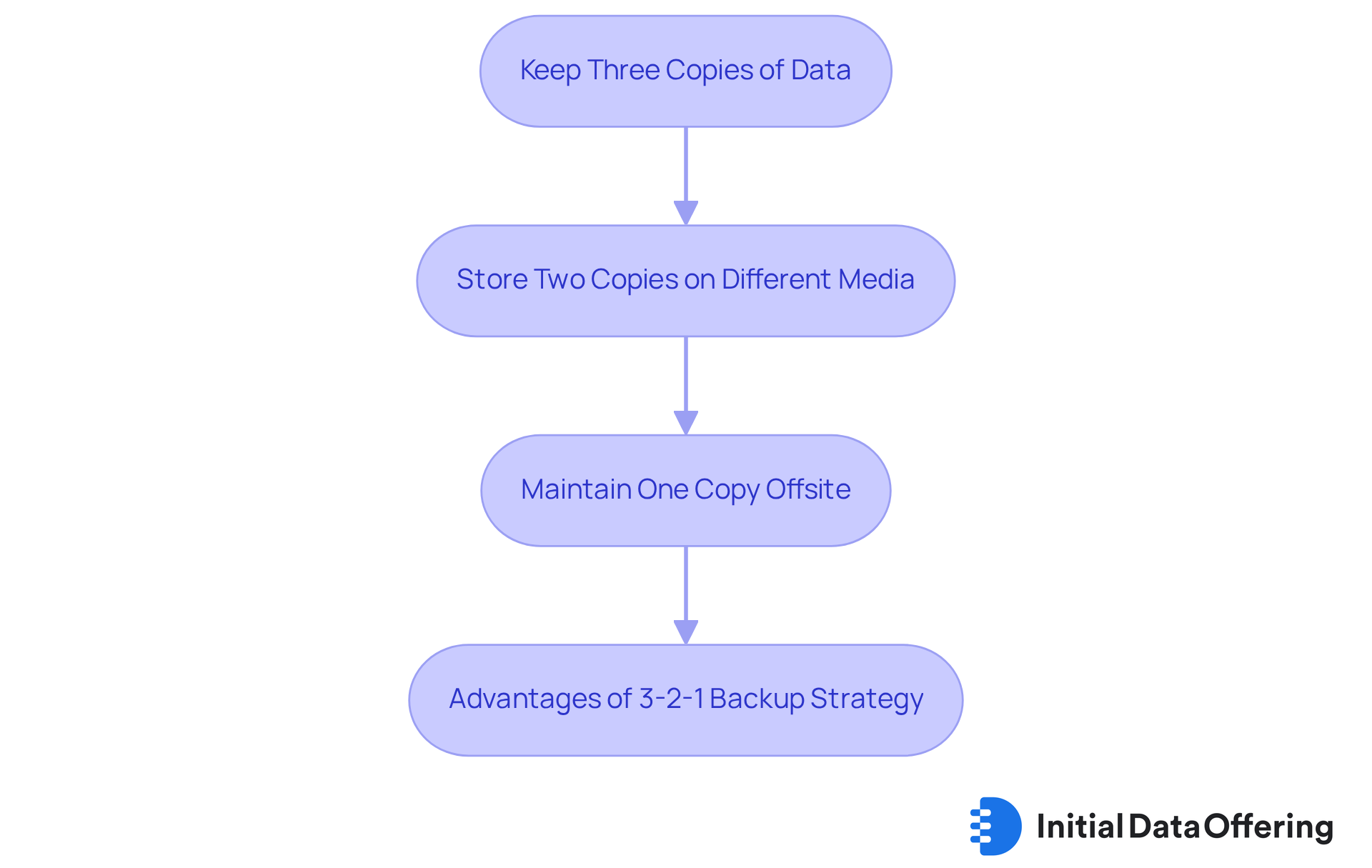
Creating a dependable data backup plan is essential for information security. The 3-2-1 backup rule is a pivotal guideline that businesses should implement:
- Keep three copies of data.
- Store two copies on different media.
- Maintain one copy offsite.
As Acronis states, "You create three copies of your data - the original data on your primary device and at least two copies." This strategy not only protects against data loss but also enhances overall resilience against cyber threats.
Why is this important? Regularly testing backup restoration processes ensures that data can be recovered quickly in the event of a cyber incident. With 80% of companies experiencing an increase in the frequency of cloud attacks, the need for robust backup strategies has never been more critical. The 3-2-1 backup rule, which has been a cornerstone of modern data protection strategies for nearly two decades, provides a clear framework for safeguarding valuable information.
In summary, implementing the 3-2-1 backup rule offers significant advantages:
- It minimizes the risk of data loss.
- It ensures quick recovery.
- It fortifies defenses against cyber threats.
By adopting this approach, businesses can enhance their data security posture and maintain operational continuity.
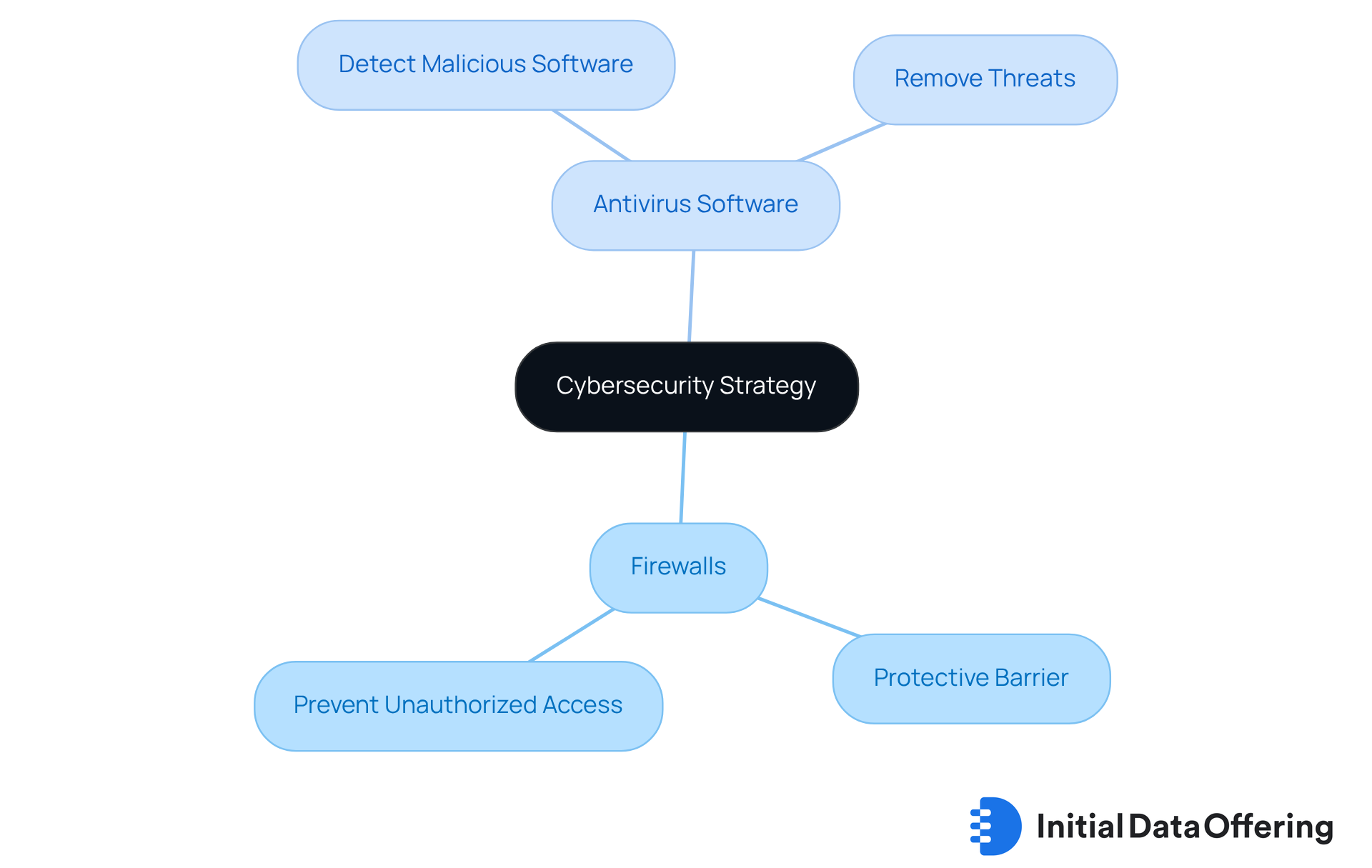
Utilize Firewalls and Antivirus Software
A comprehensive small business cybersecurity checklist should include implementing firewalls and antivirus programs as crucial elements of an online security strategy. Firewalls serve as a protective barrier between trusted internal networks and untrusted external networks, effectively preventing unauthorized access. Antivirus software plays a vital role by detecting and removing malicious software that could jeopardize systems.
Why are these tools so important? To ensure optimal protection against ever-evolving cyber threats, regular updates and proper configurations should be included in the small business cybersecurity checklist. When businesses prioritize the recommendations in the small business cybersecurity checklist, they not only safeguard their data but also enhance their overall security posture.
In summary, investing in firewalls and antivirus solutions is not just about compliance; it’s about fostering a secure environment that protects sensitive information and builds trust with clients. Are you confident that your current security measures are up to date?
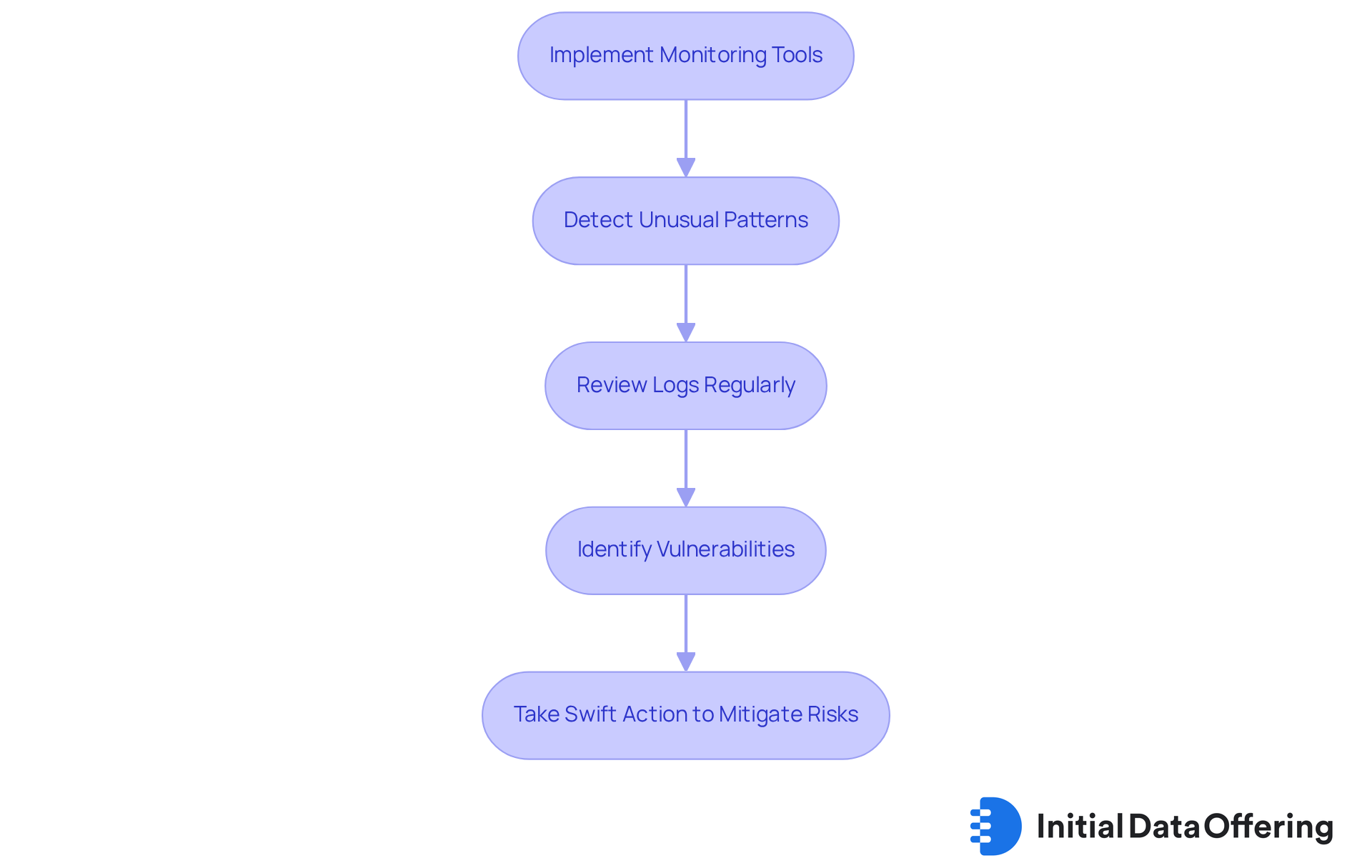
Monitor and Log Network Activity
Monitoring and logging network activity is a crucial feature for maintaining cybersecurity. By implementing tools that provide real-time visibility into network traffic, businesses can detect unusual patterns that may indicate a security breach. This advantage allows organizations to identify potential vulnerabilities through regular log reviews, enabling swift action to mitigate risks. The benefit of this proactive strategy is a significantly improved capacity to react to events efficiently, ultimately safeguarding the organization’s assets.
Have you considered how your organization monitors network activity? Regularly reviewing logs not only helps in identifying vulnerabilities but also enhances your overall security posture. By staying ahead of potential threats, you can ensure a safer environment for your operations. This approach not only protects your data but also fosters trust among your clients and stakeholders.
Create an Incident Response Plan
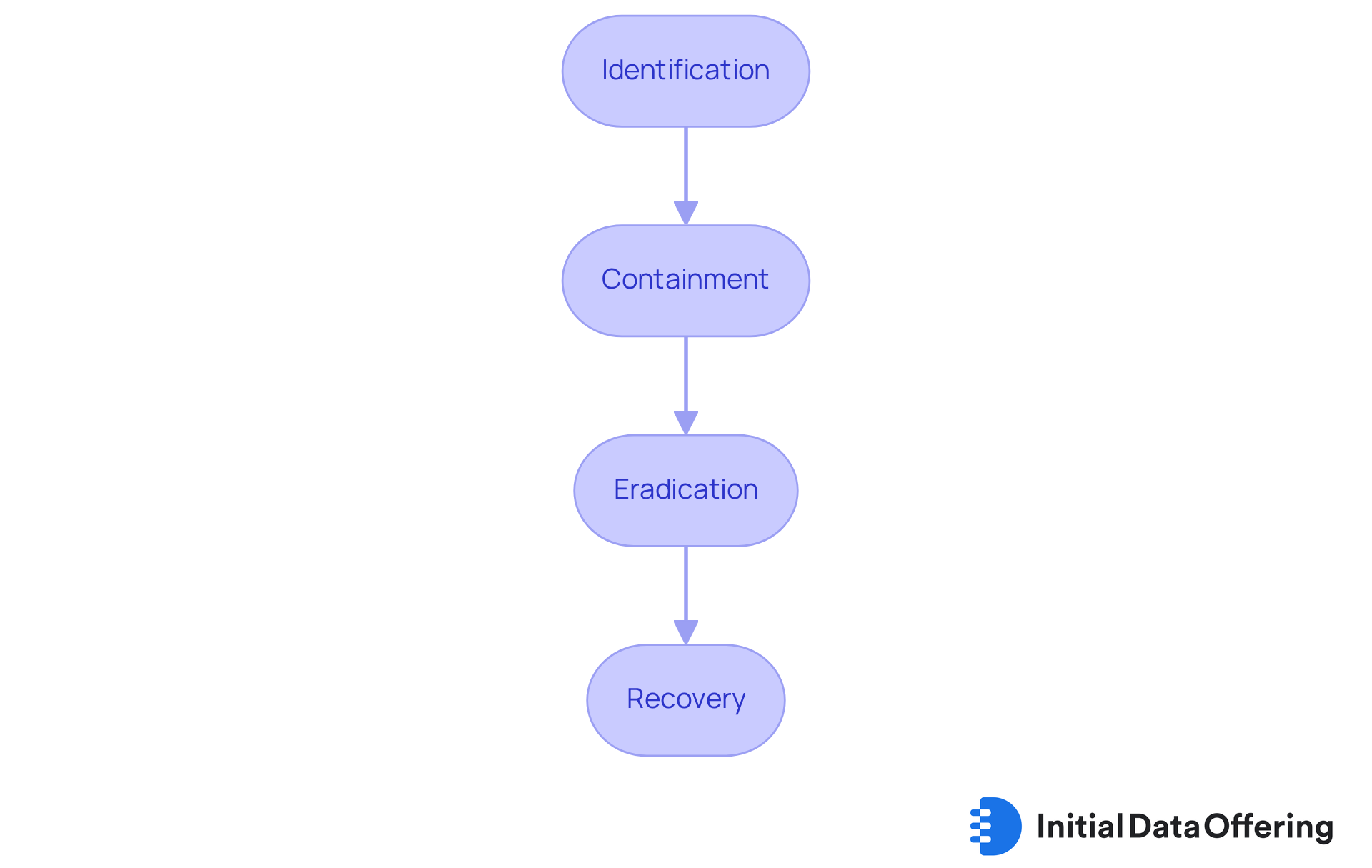
Developing a response plan is crucial for small enterprises, which should include a small business cybersecurity checklist to handle cybersecurity events effectively. This plan should clearly outline the steps to take in the event of a breach, including:
- Identification
- Containment
- Eradication
- Recovery
By conducting consistent exercises and revising the strategy, all staff members can become familiar with their responsibilities during an event.
Studies indicate that organizations performing response exercises at least every three months can react to events 35% quicker. This significant improvement not only reduces potential harm but also ensures business continuity. Furthermore, companies utilizing SOAR solutions can manage threats four times faster than those relying on manual reactions. This underscores the importance of automation in responding to events.
Transparent communication protocols during crises are vital for effective teamwork and event management. Have you considered how clear communication can enhance your team's response? Additionally, establishing a retainer with a trusted partner can bolster incident response capabilities, providing access to expert support when needed. As Mark Nicholls, Chief Research Officer, emphasizes, 'Preparedness is not built in the moment. It is earned through repetition, review, and refinement.'
In summary, having a small business cybersecurity checklist ensures that your organization is well-prepared for potential breaches and enhances overall resilience. By prioritizing regular training and leveraging automation, small enterprises can significantly improve their cybersecurity posture.
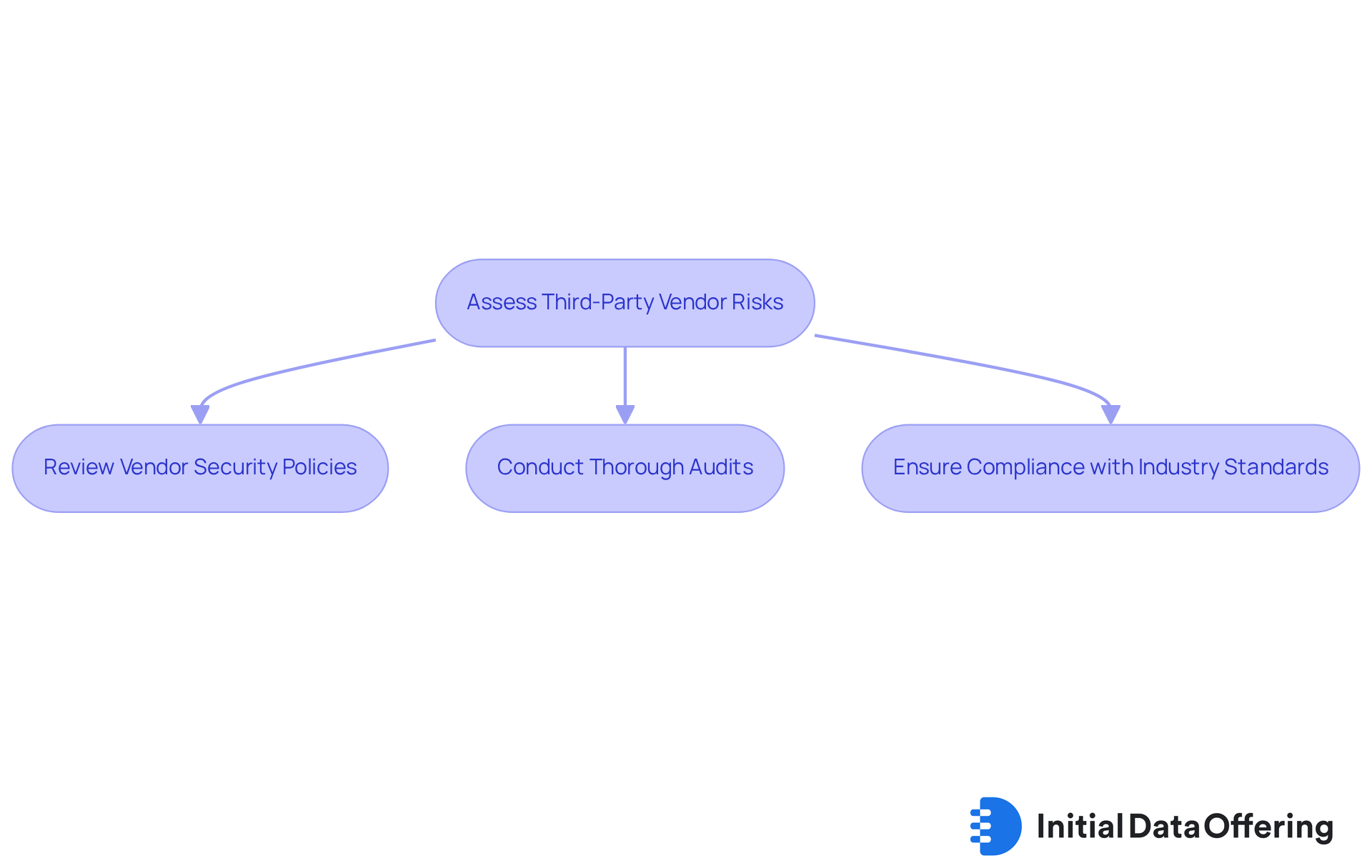
Assess Third-Party Vendor Risks
Assessing third-party vendor risks is essential for a robust cybersecurity strategy. Businesses must evaluate their vendors' protection measures to uncover potential vulnerabilities that cybercriminals might exploit. This assessment involves:
- Reviewing vendor security policies
- Conducting thorough audits
- Ensuring compliance with industry standards
Why is this important? Understanding the risks tied to third-party relationships allows businesses to implement effective measures to mitigate threats and safeguard sensitive data. By identifying weaknesses, organizations can proactively address vulnerabilities, enhancing their overall security posture.
Incorporating these assessments not only protects data but also builds trust with clients and partners. As cyber threats continue to evolve, staying ahead of potential risks is crucial. How prepared is your organization to handle third-party vendor risks?
Conclusion
Implementing a comprehensive cybersecurity checklist is crucial for small businesses that want to protect their digital assets and ensure operational continuity. By focusing on essential measures - like data analysis through unique datasets, developing robust cybersecurity policies, and fostering a culture of security awareness among employees - organizations can significantly bolster their defenses against cyber threats.
Key strategies outlined in this article include:
- The importance of regular employee training
- Strong password policies
- Multi-factor authentication
- Timely software updates
- Reliable data backup strategies
Moreover, monitoring network activity and creating an effective incident response plan are vital components that cannot be overlooked. Each of these elements plays a critical role in establishing a resilient cybersecurity framework capable of adapting to the ever-evolving threat landscape.
Given the rising frequency of cyberattacks, small enterprises must take proactive steps to safeguard their operations. By prioritizing the implementation of these essential cybersecurity practices, businesses can protect sensitive information and foster trust with clients and partners. Embracing these strategies not only ensures a robust defense against potential breaches but also leads to a more secure and resilient organization.
Frequently Asked Questions
What is the Initial Data Offering (IDO) and how can it help small enterprises?
The Initial Data Offering (IDO) provides small enterprises access to unique datasets that reveal critical insights into their security landscape, including firmographics and event data. This helps companies analyze trends, identify vulnerabilities, and understand evolving cyber threats.
How can organizations utilize datasets related to security incidents?
Organizations can evaluate their protective measures against industry benchmarks using datasets related to security incidents. This comparison highlights areas for improvement and fosters a proactive approach to security.
What role does alternative data play in cybersecurity?
Alternative data can unveil insights into potential risks associated with third-party suppliers, which is crucial for maintaining a robust security posture.
Why is it important for small businesses to develop a comprehensive cybersecurity policy?
A comprehensive cybersecurity policy sets clear guidelines for data protection, defines employee roles, and outlines acceptable technology use, thereby promoting a culture of security awareness and responsibility.
What are the benefits of incorporating best practices into a cybersecurity policy?
Incorporating best practices ensures compliance with regulations like GDPR and strengthens resilience against cyber threats, as evidenced by research showing that 60% of small enterprises facing a cyber attack cease operations within six months.
What are the 5 P's of the security framework?
The 5 P's of the security framework are People, Processes, Products, Partnerships, and Performance, providing a structured approach to policy development.
How often should a cybersecurity policy be reviewed?
Regular assessments and revisions of the cybersecurity policy are crucial to adapt to emerging threats and changes in the market landscape.
What topics should be covered in regular employee cybersecurity training?
Regular employee cybersecurity training should cover recognizing phishing attempts, practicing safe internet habits, understanding the importance of strong passwords, avoiding accessing sensitive information over public Wi-Fi, and using Virtual Private Networks (VPNs).
How effective is cybersecurity training in reducing phishing attacks?
Organizations with robust security awareness training programs experience a 50% reduction in successful phishing attacks, highlighting the effectiveness of these initiatives.
What is the average cost of a data breach, and why is this significant?
The average cost of a data breach is $4.4 million, underscoring the financial rationale for investing in cybersecurity training and proactive measures to protect against potential cyber incidents.